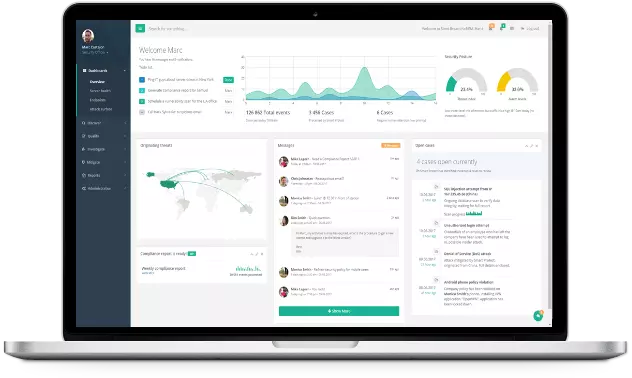
Predictive Breach Detection
See beyond your perimeter with continuous asset cataloging, IP detection and shadow IT discovery.
Quantum Armor combines the range of an EASM platform with the depth of cutting-edge DRPS.
Correlate your assets and vulnerabilities to produce actionable risk assessments.
Our Generative AI ingests thousands of data points to provide clear security briefs to secure your company.
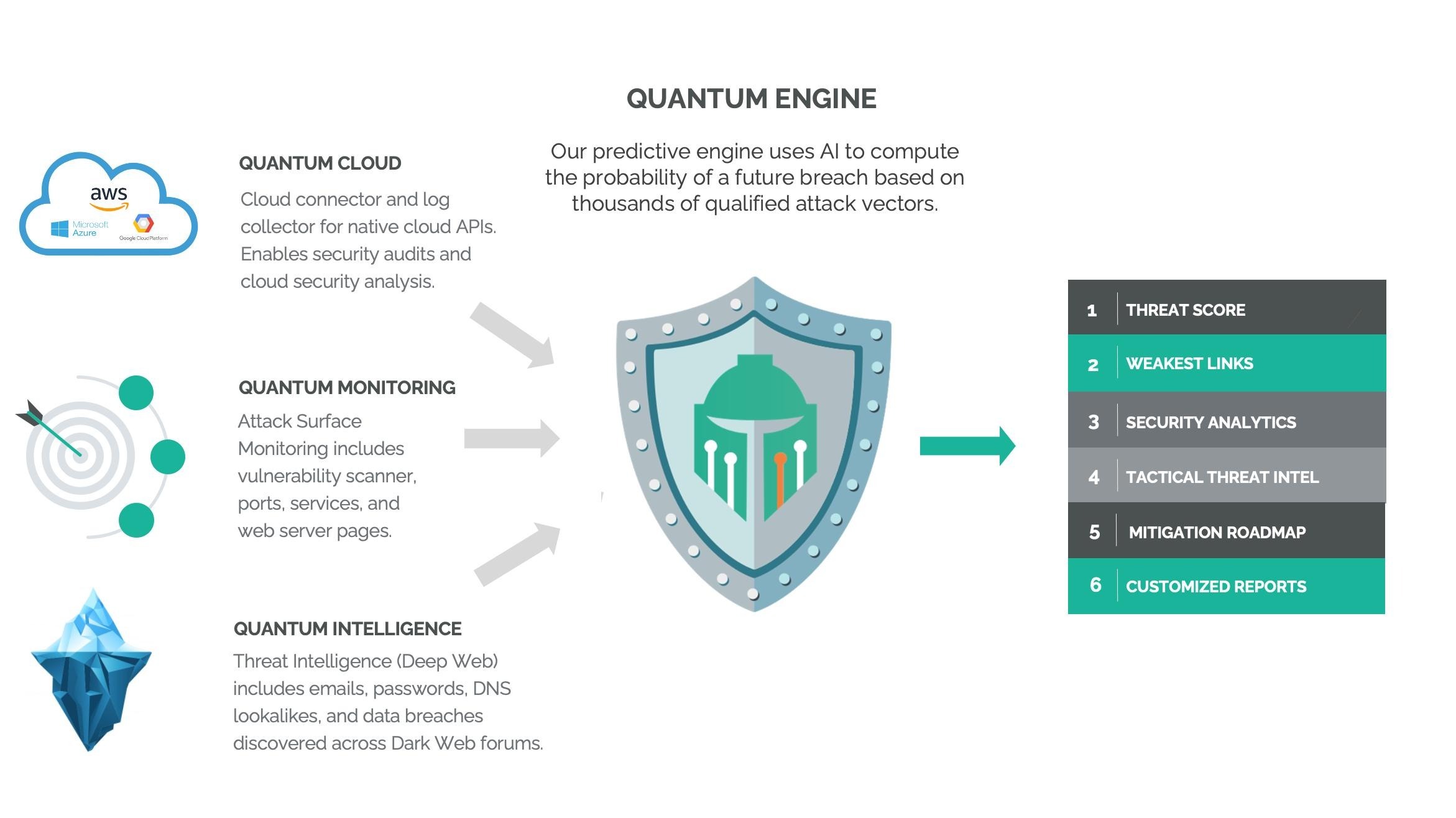
Discover the unknown
Our attack surface monitoring system doesn't require any software or agents to be installed on-target. Quantum Armor gathers information that is externally available to rate the cyber security posture of your digital assets.
Learn More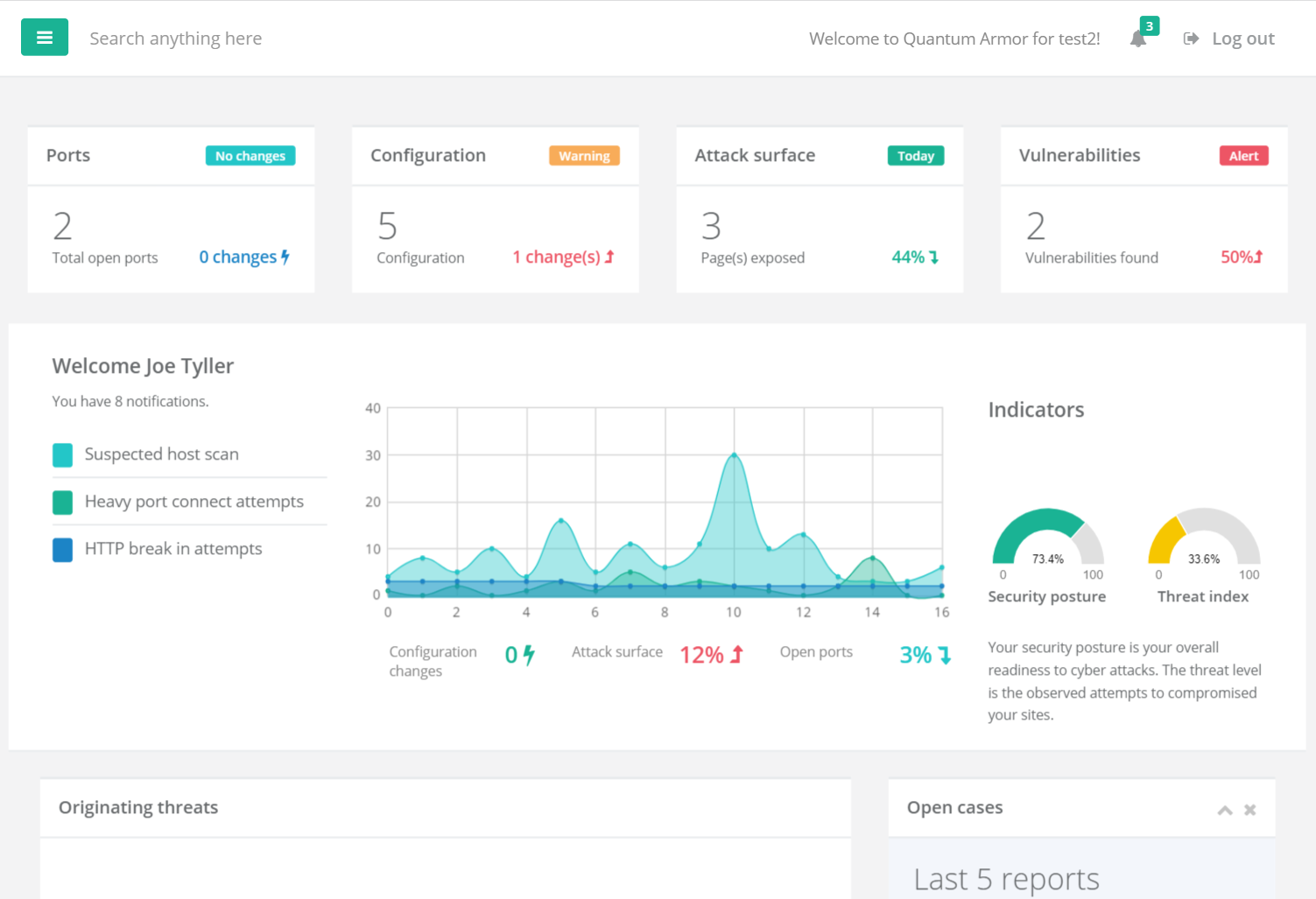
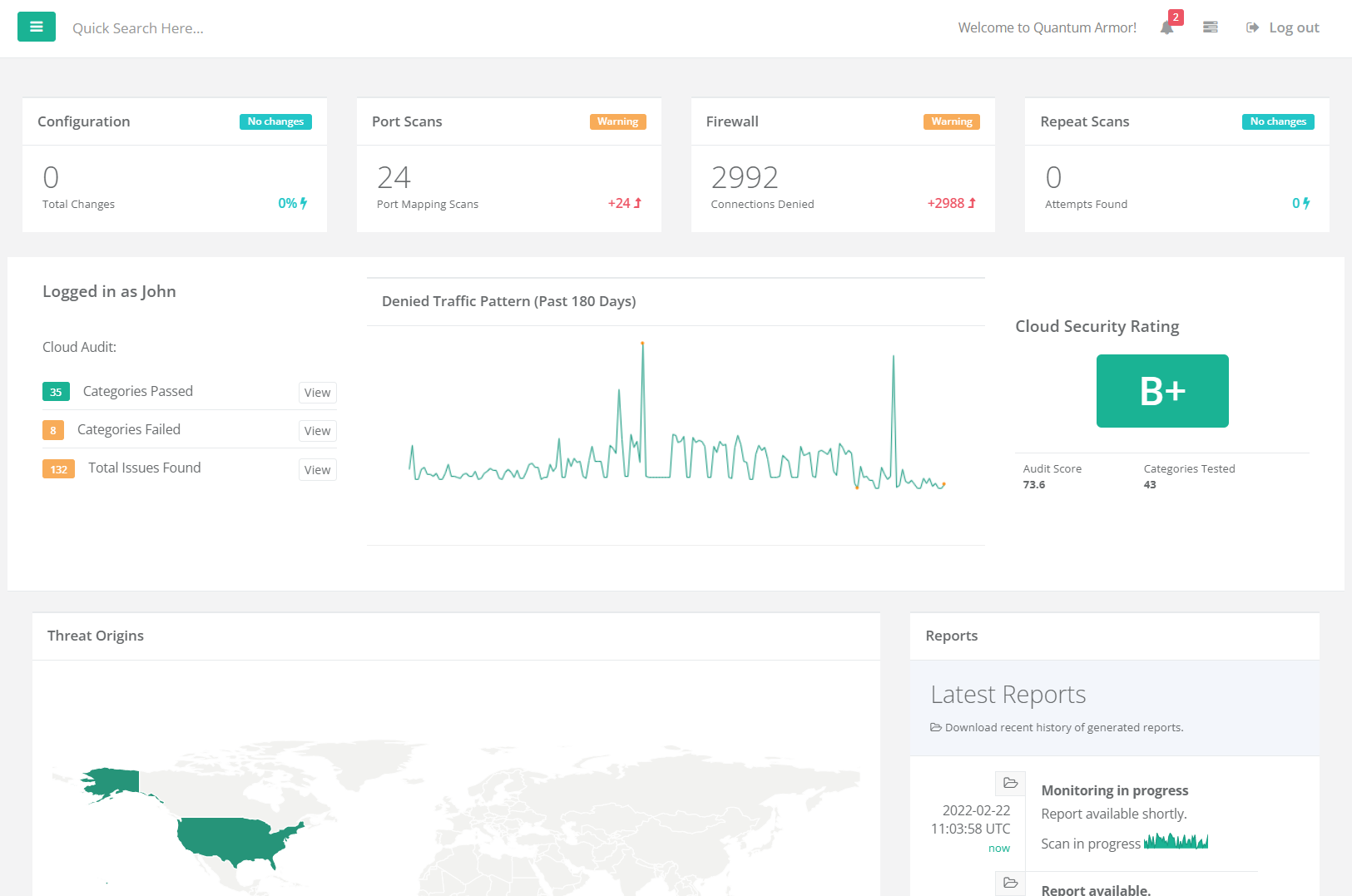
Insights Into Your Cloud Instances
Utilizing a range of proprietary algorithms, Quantum Armor helps you monitor, audit, and harden your cloud instance without installing any agents. This is done by leveraging the APIs that are already in place and provided by the cloud vendors themselves.
Learn MoreInformation is key
By partnering with NATO, Quantum Armor is capable of identifying key IoCs, malware strains and threat actors operating across the web, and then cross-reference those against your organization's logs and data.
Learn More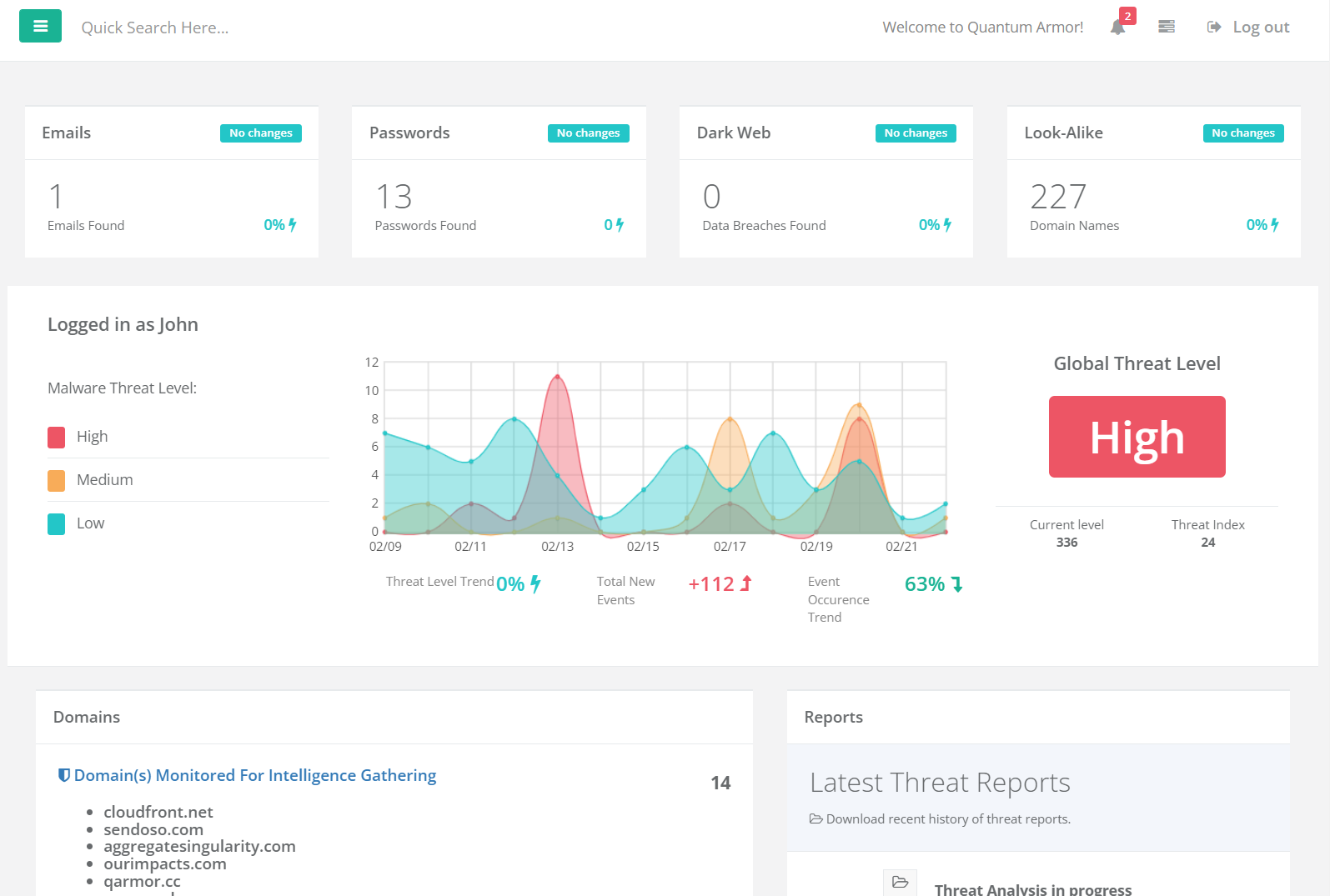
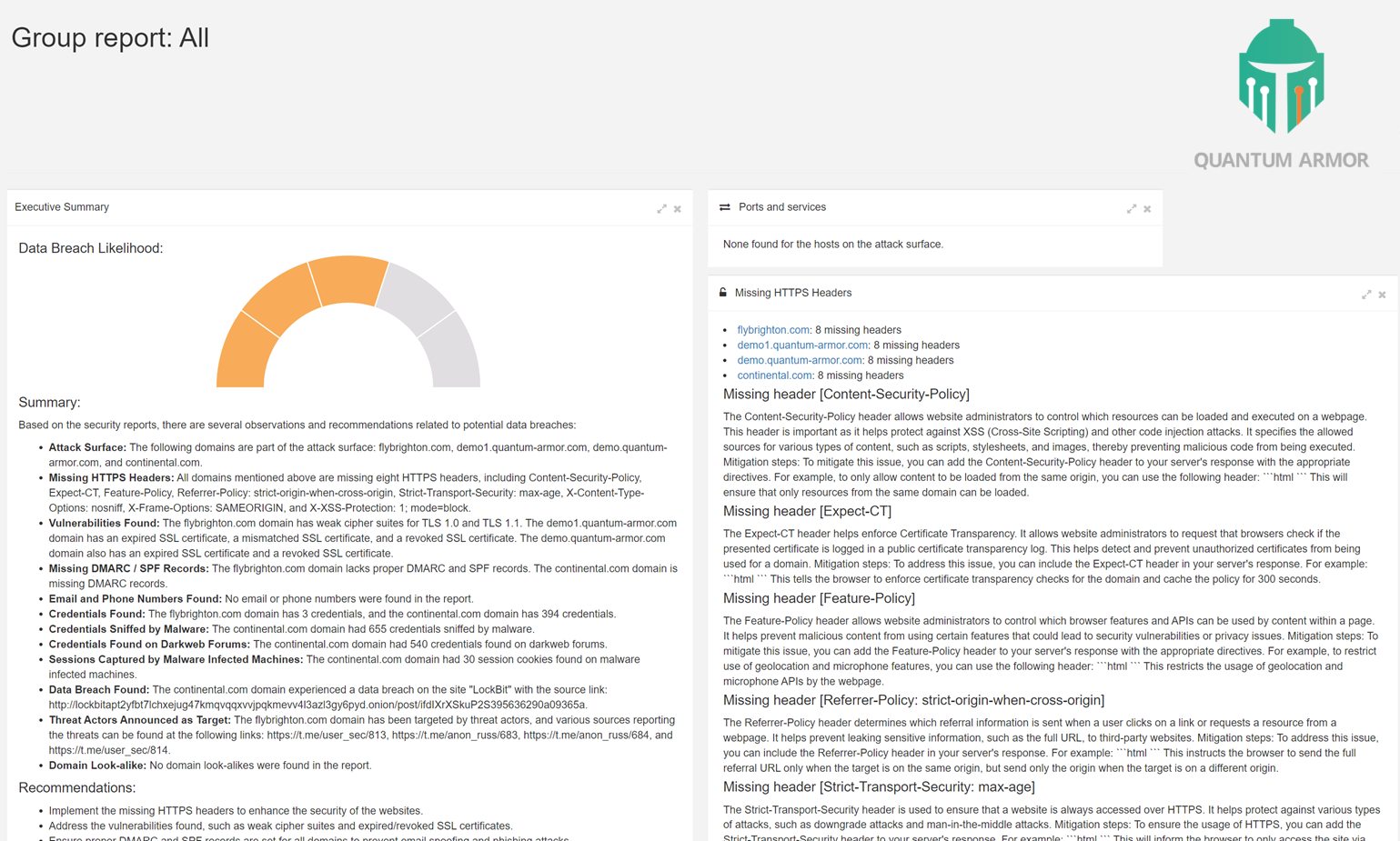
Making sense of it all
The Quantum Armor LLM ingests thousands of data points and provides a daily security brief including an executive summary, security rating, detailed findings, and recommended roadmap along with the likelihood of an imminent data breach.
Learn More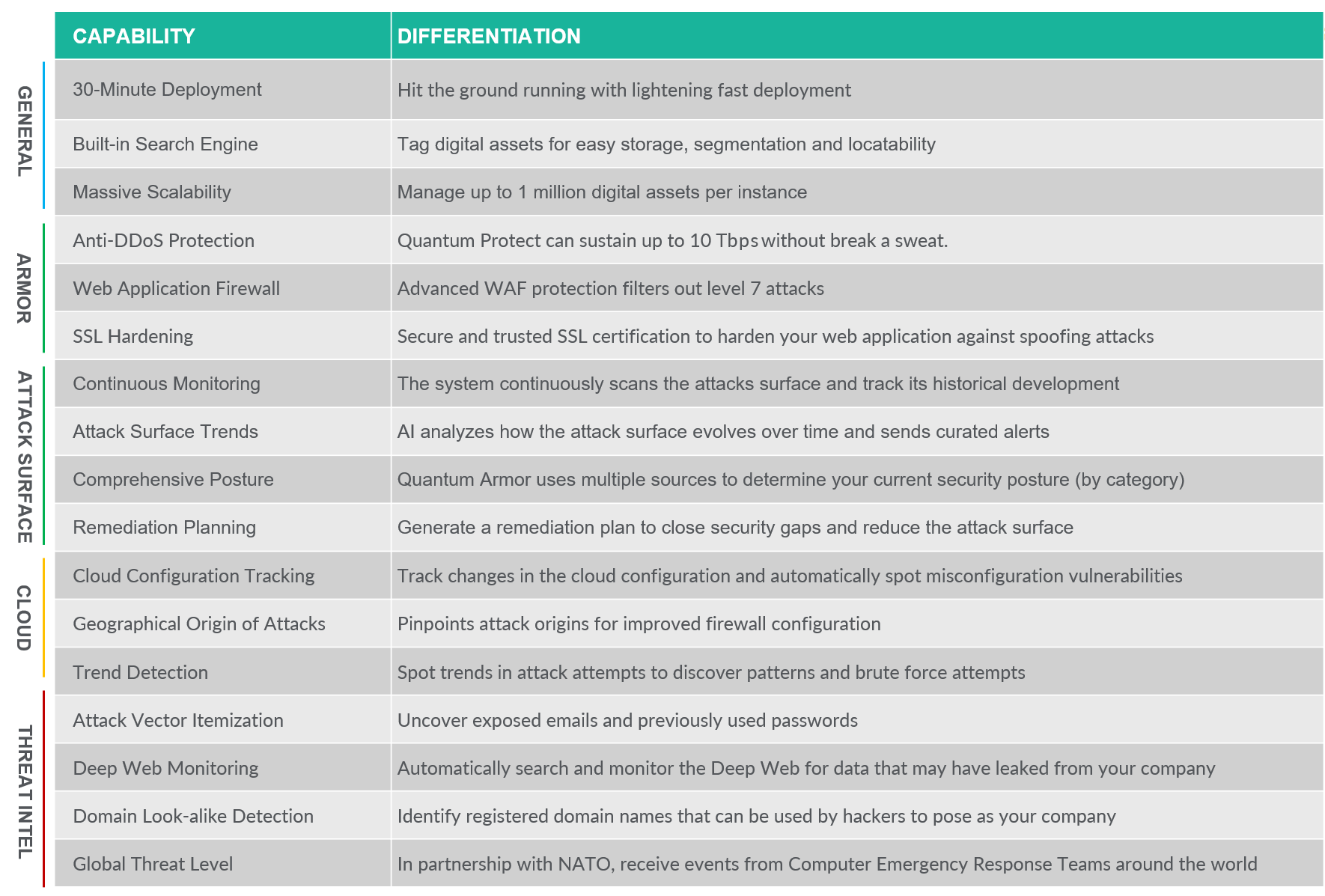
Quantum Armor™ is a Silent Breach product.
Silent Breach is a leading cybersecurity firm specializing in network security and digital asset protection.
Please visit https://silentbreach.com to learn more.
Follow us on social media
© Silent Breach
Quantum Armor micro-site. Please visit https://silentbreach.com for more information on Silent Breach.